Network security
Levering Your Business Through Our Services
BIT has a significant and proven experience in security services, dealing with complex and multi-faceted security that can address range of dynamic security threats since 1999.
We have provided protection across network, safeguarding the perimeter, critical internal assets, data, remote users, customers and partners. Our extensive security experience in banking, government, GLC, service provider and military industries can mitigate dynamic security threats and meet total cost of ownership (TCO) goals.
Our security service team is made up of industry experts and certified professionals in security services to support the complete lifecycle of security infrastructure.
Our security team can successfully plan, design, configure, deploy and support ranges of security solutions. We are able to deliver security services the way our clients operate at anytime, anyplace and anywhere. Clients require a wide range of services to meet their needs.
Our Information Security Services offering include the following:
1. Security Systems Integration
2. Security Consultancy
3. Managed Security
SECURITY SYSTEMS INTEGRATION
This service offers leading-edge and innovative security systems implementation and integration. We carry only world’s top ranking security products so that our clients have the options on getting the best solution that can meet their business and technology requirements. Our Security Systems Integration services are able to provide the following security solutions:
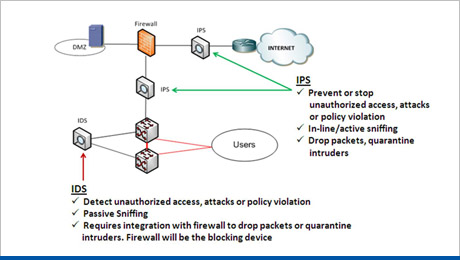
Intrusion Prevention System (IPS)
This solution can provide protection over 10,000 security threats in order to help clients secure their confidential data and meet ever-increasing compliance mandates. Intrusion Detection and Prevention accurately identifies classifies and stops malicious traffic, including worms, spyware, adware, network viruses, application abuse and hacking attempts before they affect business continuity. It also stops Day-Zero attacks before signature updates are available.
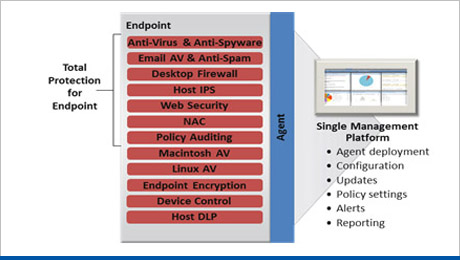
Endpoint Protection
This solution can protect endpoints (server, desktop, laptop, application) with a combination of host-based firewall, intrusion prevention, zero-update attack protection and signature-based antivirus in a single agent. This unique blend of capabilities defends servers and desktops against sophisticated zero-day attacks and enforces acceptable-use and compliance policies within a simple management infrastructure.
Secure Web Gateway
This solution can protect web-surfing desktops from infection and enforce company policies. This solution comes with a combination of next-generation security technology on a single platform :
- Web filtering , Web antimalware , Content filtering
- Application control , Accelerated applications , Proxy authentication , Caching

Unified Threat Management
This solution can provide comprehensive multiple security functions in one single appliance. This solution is meant for small and medium businesses, which can reduce cost and complexity by providing the following security components in one single appliance:

Network Access Control
This solution enables client to enforce network security policies on all devices seeking to access the network, either the devices are managed or unmanaged. This solution also does the following enforcement:
- Confirms a user’s identity before access to the network is granted
- Noncompliant devices can be quarantined and brought into compliance, for example a workstation doesn’t have a latest antivirus or Microsoft patches can be quarantine and redirect to local update server before it can access the network
- Supports the entire guest access control lifecycle at client premises (provisioning, notification, management and reporting).

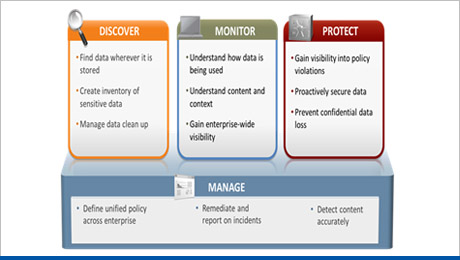
Data Loss Prevention
This solution can enforce better business practices concerning handling and transmission of sensitive data. This solution will discover, monitor, protect, and control network access and enforce content policies wherever it is stored or however it is used. This content-aware solution is able to classify information content that:
- Contained within an object
- In use during an operation
- In motion across a network
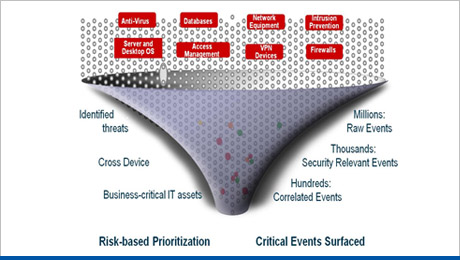
Security Information & Event Management
This solution can provide real-time monitoring and historical reporting of security events from networks, systems and applications. This solution will be able to improve security operations, threat management and incident response capabilities within an organization. This solution shall be able to correlate security event from multivendor products and report true positive detected event.
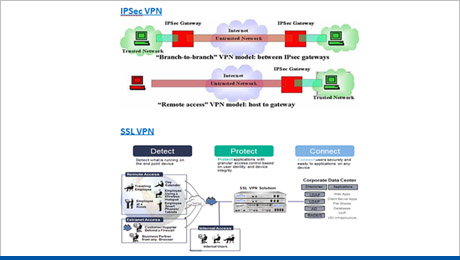
Secure Communication
This solution can protect privacy and integrity of information through business communications. We deploy fast, reliable and secure connectivity for remote offices, business partner locations and other branch sites. The data, voice and video communications between locations are kept confidential across untrusted networks
- Virtual Private Tunnel
- Traffic Encryption
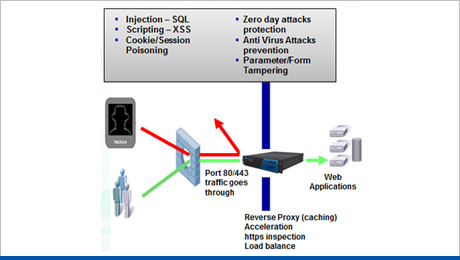
Web Application Firewall
This solution can protects Web applications and Web services against hackers leveraging protocol or application vulnerabilities to instigate data theft, denial of service or defacement of your Web site. It also can increase the web access performance and scalability of these applications.
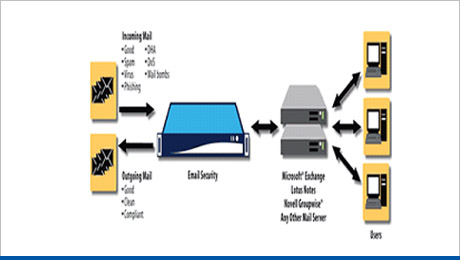
Email Security
This solution can provide the highest level of inbound and outbound e-mail security available today. This solution includes the following security technology:
- Reputation authority , Malware prevention
- Spam prevention , Content filtering , Email encryption
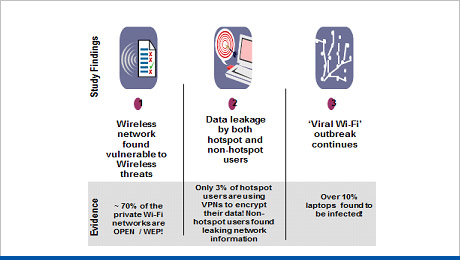
Wireless Security
This solution can protect wireless connection with combination of layered security approach:
- Hidden SSID , MAC Address Registration
- Radius Authentication / LDAP Server
- Encryption , Firewall
- Intrusion Prevention System
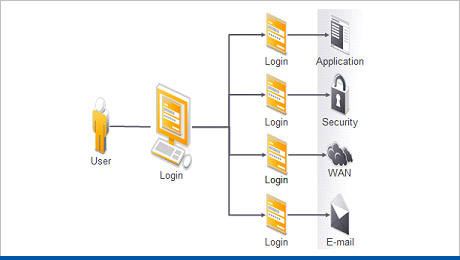
Identity & Access Management
This solution can provide password management system to create a single sign-on (from multiple applications access) for improved productivity and security. It features:
- Control multiple access based on identity
- Single login for multiple application access
- Synchronize passwords and accounts within the various back end systems
- Self-service password management
Two Factor Authentication
This solution can provide an additional strong authentication when accessing systems or applications. This solution avoids compromised credentials from being used. It features:
- OTP (One-time password) authentication device with LCD display, battery, and OTP generation button
- Password is generated on demand
- Password can be configured to expire in minutes/seconds
SECURITY CONSULTANCY
BIT Security Consultancy service offers security assessment and improvement of current security posture. BIT has a history for providing security consulting services in the following security consulting areas:
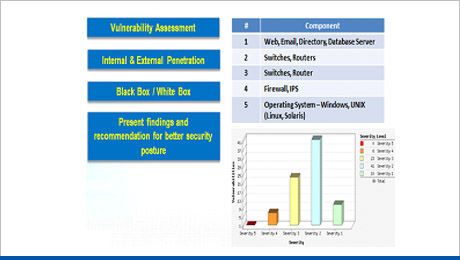
Security Posture Assessment
This service can discover current network and systems security weaknesses with the goal of improving security posture. Our activities and deliverables for this security services include:
- External Penetration Test
- Black Box Testing (Zero Knowledge)
- White Box Testing (Complete Knowledge)
- Vulnerability assessment – Network & security devices, servers, OS, web server & web application
- Internal penetration test
- Present findings for the discovered weaknesses & recommendations for better security posture
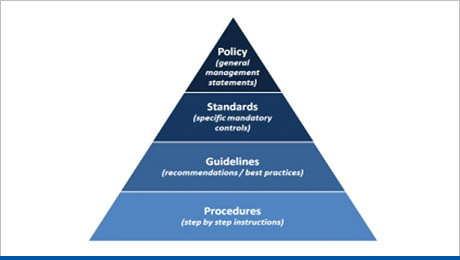
Security Policy Documentation
This solution can protect endpoints (server, desktop, laptop, application) with a combination of host-based firewall, intrusion prevention, zero-update attack protection and signature-based antivirus in a single agent. This unique blend of capabilities defends servers and desktops against sophisticated zero-day attacks and enforces acceptable-use and compliance policies within a simple management infrastructure.
- Gather information
- Review security requirements, goals and objectives
- Develop document (Policy, Procedure, Standard, Guideline)
- Document review & signoff
MANAGED SECURITY
BIT Intrusion Analysis service will ensure that security devices are always healthy and able to perform their tasks without performance drop. The services include monthly or weekly intrusion analysis with the following deliverables:
- Review and analyse security logs
- Impact assessment
- Classify event as True Positive or False Positive
- Determine the necessary action (allow or block) for the detected attacks
- Tune or optimize the signature or configuration
- Recommend User Action to clean, quarantine or prevent future exploits.









